ParaSoft
HOME Insure++
Quick facts |
Insure++: An Automatic Runtime Error Detection ToolFor a printable version, click here. Table of Contents
2. How Insure++ Works 3. How to Use Insure++ 4. What Insure++ Finds
4.1.2 Pointer Abuse 4.1.3 Memory Leaks 4.1.4 Dynamic Memory Manipulation 4.1.5 Strings
4.2.2 I/O Statements 4.2.3 Mismatched Arguments 4.2.4 Invalid Parameters in System Calls 4.2.5 Unexpected Errors in System Calls 6. Availability 7. Contacting ParaSoft 1. IntroductionInsure++ is an automatic runtime error detection tool for C/C++ applications that uncovers problems such as memory corruption, memory leaks, pointer errors, and I/O errors. By using a unique set of patented technologies, Insure++ thoroughly examines and tests the code from inside and out, then reports errors and pinpoints their exact location. Insure++ also performs coverage analysis, clearly indicating which sections of the code were tested, and facilitates memory optimization, displaying how the program uses memory in real-time. By integrating Insure++ into your development environment, developers can save weeks of debugging time and prevent costly crashes from affecting your customers. Unfortunately, development tools like Insure++ usually aren't called into action until the end of a software project, when particularly difficult bugs causing erratic behavior cannot be found. The typical crisis cycle goes something like this: developers exhaust all options searching for the source of a bug, they give up, they use Insure++, Insure++ finds the bug, the developers fix the bug, and then move on until the next crisis hits. This crisis cycle could be broken, resulting in less aggravation and less time spent debugging, if Insure++ was incorporated into the software development process earlier. Insure++ has been used on C/C++ applications with hundreds of thousands of lines of code; multi-process applications, programs distributed over hundreds of workstations, operating systems, and compilers have been validated with Insure++. This paper describes Insure++'s modes of operation, how to implement Insure++ in the development process, and the types of errors Insure++ uncovers. 2. How Insure++ WorksInsure has two modes of operation that provide developers with varying degrees of error checking: Chaperon for a quick check and Source Code Instrumentation for deep error checking. This gives developers a large amount of flexibility when it comes to maximizing their development and debugging time. In both modes, when Insure++ finds a problem, it provides a complete diagnosis, including the names of related variables, the line of source code containing the error, a description of the error, and a stack trace. 2.1 ChaperonInsure++'s latest technology--Chaperon--works with existing executable programs. Chaperon does not require any recompiling and relinking, or changing of environment variables. Though less intensive than Source Code Instrumentation mode, Chaperon is more expedient. It checks all data memory references made by a process, whether in compiled code, language support routines, or shared or archived libraries. It also detects and reports reads of uninitialized memory, reads or writes that are not within the bounds of allocated blocks, and allocation errors such as memory leaks.
Chaperon also detects memory blocks that have been allocated and not freed. Such a block is "in use." If a block is in use and cannot be reached by starting from the stack, or statically allocated regions, and proceeding through already reached allocated blocks, then the block is a "memory leak." The block could not be freed without some pointer to specify its address as the parameter to When Chaperon detects improper behavior, it issues an error message identifying the kind of error and the place where it occurred. Improper behavior is considered to be any access to a logically unallocated region, a Read (or Modify) access to bytes that have been allocated but not yet Written, and errors or abuses of the malloc/free protocol, such as attempting to free the same block twice. 2.2 Source Code InstrumentationWhen a more in-depth analysis of the code is required, use the Source Code Instrumentation mode. This mode provides comprehensive memory and error checking through the creation of an instrumented executable of the program. Utilizing the techniques of Source Code Instrumentation (SCI) (patent #5,581,696) and Runtime Pointer Tracking (RPT) (patent # 5,842,019) to develop a comprehensive knowledge of the software, Insure++ builds a database of all program elements, including data structures, memory usage, pointer usage, and interfaces. Source Code Instrumentation parses, analyzes, and converts the original source code into a new, equivalent source code. The equivalent code is stored in a temporary file that is passed to the compiler, which generates the object code. Throughout the process, the original source code file is not modified and the entire procedure does not require any user intervention. Once all of the files in the project are instrumented, they are linked into a final executable, which is then ready for runtime error detection. During compilation Insure++ inserts test and analysis functions around every line of source code. At runtime Insure++ checks each data value and memory reference against its database to verify consistency and correctness. Because Source Code Instrumentation allows Insure++ to get deep inside the application under test, it is significantly more precise and thorough than object-level technologies. 2.2.1 Mutation TestingThe Source Code Instrumentation mode also uses Mutation Testing, which is the process of rewriting source code to flush out ambiguities that can cause errors, such as bad copy constructors. Insure++ reads the source code and writes out new source code that is functionally equivalent to the original code but also contains error checking code. During the error-detection process, the "functionally equivalent" mutants are run in place of the original source code. If the original program does not contain problems, the mutants should not perform any differently than the original program. A mutant that performs differently than the original code indicates a serious error in the original program. Through this method, Insure++ is able to uncover ambiguities that are difficult to detect with any other method or tool. This is particularly important in C++. For example, Mutation Testing can detect the following types of errors:
2.2.2 Runtime Pointer Tracking
This technology checks every read and write to memory against an accumulated database of pointers and blocks. As memory management commands such as 2.3 Additional Features2.3.1 Coverage Analysis with TCAThe Total Coverage Analysis (TCA) add-on works hand-in-hand with Insure++. It lets developers get "beneath the hood" of the program to see which parts are actually tested and how often each block is executed. In conjunction with Insure++, this can improve the efficiency of testing and help developers shorten the time required to deliver more reliable programs. Coverage analysis information is automatically built in whenever a project is instrumented with Insure++. TCA groups code into logical blocks, where a block is a group of statements that must always be executed as a group. For example, the following code has three statements, but only one block. i = 3; j = i+3; return i+j; Because TCA reports coverage by blocks instead of lines, developers don't need to analyze as much data and they can actually see which paths and statements have been executed. For more information, please refer to our white paper, Maximizing Test-Suite Coverage: The TCA Solution. 2.3.2 Memory Optimization with InuseIt can be difficult to fully understand the implications of dynamically allocating memory blocks in a program. Inuse is a graphical utility that allows developers to watch how a program handles memory in real-time. Inuse allows developers to:
For more information, please refer to our white paper, Avoiding Dynamic Memory Problems: A New Solution for Developers. 2.3.3 ThreadsInsure++ can "run" multi-threaded applications and detect errors in the threads. Insure++ is able to instrument all threads, track all processes in the application, quickly pinpoint problems, and report specific information on errors found. Insure++ allows developers of multi-threaded applications to rapidly find and fix bugs that would otherwise remain hidden in threads and cause the application to perform incorrectly, or fail to perform at all. For more information, please refer to our white paper, Threads++: A New Solution to the Multithreading Dilemma. 3. How to Use Insure++Insure++ can be used during the development process to detect errors and prevent them from causing even bigger problems near the end of the project. The earlier Insure++ is used in the development process the better. You can incorporate Insure++ into the nightly builds that automatically build the application every night. The minimal nightly build should pull all necessary code from the source code repository, clean and compile that code, then build the application. The ideal nightly build should also run all available test cases (both unit test suites and application test suites, including Insure++) and report any failures that occur. At least, this process minimizes the overhead involved in assembling the application pieces. At best, it ensures that the application continues to run as expected and detects any errors introduced by newly integrated code. If Insure++ cannot be used on a daily basis, it can also be used in another way. For example, say there is an error that is causing a program to crash. The following procedure provides a plan of attack for finding the crash-causing error.
If no errors are reported in Chaperon mode, start using Source Code Instrumentation to instrument each file, one by one, where the error might be located.
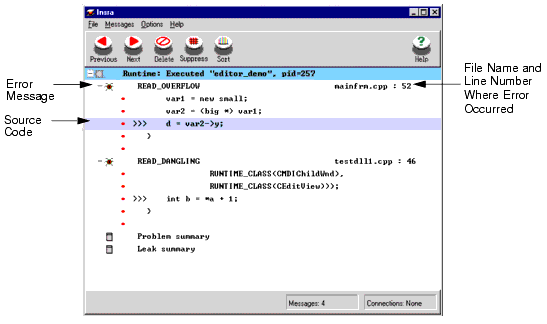
The example below illustrates how more errors are uncovered in an application as the level of error detection is increased. Note: In this section, the error messages are taken from the Windows NT version of Insure++ as displayed in the Insra window. The Insra window is also available in the UNIX versions. 3.1 Using ChaperonFor situations that require a quick overview of the code, Chaperon gives developers a fast, accurate analysis while uncovering extremely complex errors such as memory leaks, memory reference errors, and memory corruption.
For example, say we have a program that is a simple text editor called The messages are displayed in the Insra error display GUI. The READ_OVERFLOW message refers to a structured reference that is out of range. The READ_DANGLING message refers to an attempt to perform a read from a dangling pointer. Double-clicking the error message opens a message window (shown in Figure 2) that displays more detailed information about the error message, as well as the stack trace. 3.2 Using Source Code InstrumentationIn the previous section Chaperon was used on an executable. Chaperon provides a very effective mode of error detection, but is not quite as thorough as Source Code Instrumentation. Though Source Code Instrumentation is more extensive in its testing functions than Chaperon, it can be much slower.
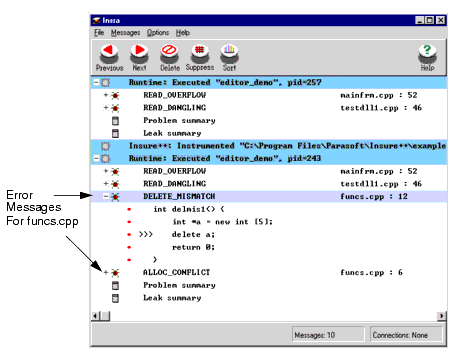
To minimize the time necessary for testing, developers do not have to instrument the entire application with Insure++; they can instrument one file at a time. Using the same example we used in the section for Chaperon ( #include <stdlib.h> int alloc1() { char *a; a = new char; free(a); return 0; } int delmis1() { int *a = new int [5]; delete a; return 0; } When the application is recompiled, relinked, and run with Insure++, two new errors are reported by Insure++ in the Insra display window, as shown in Figure 4.
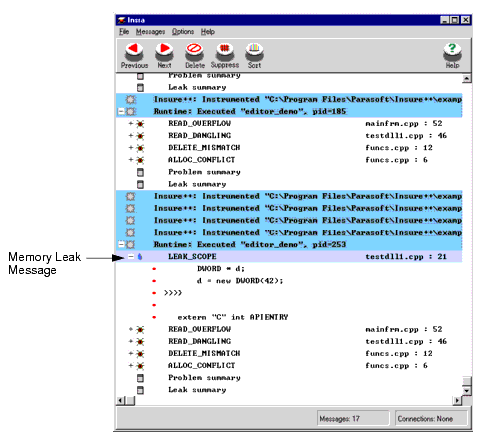
The errors found in This additional error is for memory leak leaving scope. A function contains a local variable that points to a block of memory but the function returns without saving the pointer in a global variable or passing it back to its caller. 4. What Insure++ FindsInsure++ finds elusive types of errors in C/C++ applications. Most of these errors fall into three major categories:
Note: The error messages displayed in this section are taken from the standard UNIX version of Insure++. 4.1 Memory Reference ErrorsInsure++ checks all types of memory references, including those to static (global), stack, and shared memory, as well as dynamically allocated memory. Even programs that compile, produce correct results, and have a large commercial distribution can contain memory reference errors. These errors are land mines in the memory space, lying dormant until a program accesses the erroneous memory location(s), causing the program to execute incorrectly or crash. 4.1.1 Memory CorruptionThese errors can be particularly unpleasant, especially if they are well-disguised. For example, the program shown in Figure 6 concatenates the arguments given on the command line and prints the resulting string. When compiled with a typical compiler and run, the expected results appear. 1: /* 2: * File: hello.c 3: */ 4: main(argc, argv) 5: int argc; 6: char *argv[]; 7: { 8: char str[16]; 9: int i; 10: 11: str[0] = '\0'; 12: for(i=0; i<argc; i++) { 13: strcat(str, argv[i]); 14: if(i < (argc-1)) strcat(str, " "); 15: } 16: printf("You entered: %s\n", str); 17: } If Figure 7 were the extent of your test procedures, you would probably conclude that this program works correctly. However, it has a very serious memory corruption error. $ cc -o hello hello.c $ hello world You entered: hello world $ hello cruel world You entered: hello cruel world
If you compile the program with Insure++, the command " [hello.c:13] **WRITE_OVERFLOW** >> strcat(str, argv[i]); Writing overflows memory: str bbbbbbbbbbbbbbbbbbbbbbbbbbbb | 16 | 2 | wwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwww Writing (w) : 0xf7fff8a8 thru 0xf7fff8b9 (18 bytes) To block (b) : 0xf7fff8a8 thru 0xf7fff8b7 (16 bytes) str, declared at hello.c, 8 main() hello.c, 13 **Memory corrupted. Program may crash!!** [hello.c:16] **READ_OVERFLOW** >> printf("You entered: %s\n", str); String is not null terminated within range: str Reading : 0xf7fff8a8 thru 0xf7fff8b9 (18 bytes) From block : 0xf7fff8a8 thru 0xf7fff8b7 (16 bytes) str, declared at hello.c, 8 main() hello.c, 16 You entered: hello cruel world
Insure++ finds problems related to overwriting memory or reading past the legal bounds of an object, regardless of whether it is allocated statically (through a global variable), locally on the stack, dynamically (with 4.1.2 Pointer AbuseProblems with pointers are among the most difficult encountered by C and C++ programmers. Insure++ detects pointer-related problems in the following categories:
Figure 9 shows the code for a second version of the " 1 /* 2: * File: hello.c 3: */ 4: #include <malloc.h> 5: 6: main(argc, argv) 7: int argc; 8: char *argv[]; 9: { 10: char *string, *string_so_far; 11: int i, length; 12: 13: length = 1; /* Include last NULL */ 14: 15: for(i=0; i<argc; i++) { 16: length += strlen(argv[i])+1; 17: string = malloc(length); 18: /* 19: * Copy the string built so far. 20: */ 21: if(string_so_far != (char *)0) 22: strcpy(string, string_so_far); 23: else *string = '\0'; 24: 25: strcat(string, argv[i]); 26: if(i < argc-1) strcat(string, " "); 27: string_so_far = string; 28: } 29: printf("You entered: %s\n", string); 4.1.3 Memory LeaksMemory leaks can be extremely difficult to detect because they can take days of continuous execution to cause a failure. Small leaks in low level routines can mean that the function might be called thousands or even millions of times before it loses enough memory to crash the system. This is exactly the type of subtle bug that survives in-house testing only to show up when a customer uses the program for some enormous processing task.
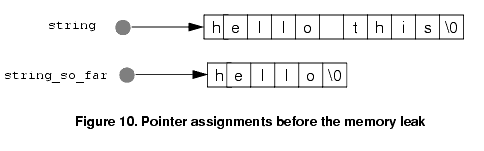
A memory leak occurs when a piece of dynamically allocated memory can no longer be freed because the program no longer contains any pointers to that block. A simple example of this behavior can be seen by running the (corrected) " hello this is a test If we examine the state of the program just prior to execution of line 27 (Figure 9), we find:
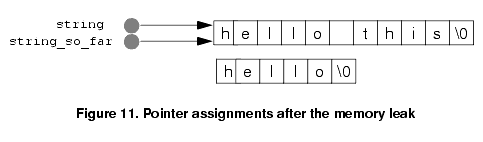
These assignments are shown schematically in Figure 10 - both variables point to different blocks of dynamically allocated memory. string_so_far = string; both variables are made to point to the longer memory block, as shown in Figure 11.
Once this has happened, there is no remaining pointer that points to the shorter block. There is now no way that the memory that was previously pointed to by [hello.c:27] **LEAK_ASSIGN** >> string_so_far = string; Memory leaked due to reassignment: string Lost block: 0x0001fbb0 thru 0x0001fbb6 (7 bytes) string, allocated at hello.c, 17 Stack trace where the error occurred: main() hello.c, 27
Since this error is caused when a pointer is re-assigned, it is known as
4.1.4 Dynamic Memory Manipulation
With dynamically allocated memory, programs often continue running after a programming error corrupts the memory; sometimes they don't crash at all. One common mistake is trying to reuse a pointer after it has already been In addition to dangling pointers, Insure++ detects many other dynamic memory bugs including:
Insure++ also helps uncover dynamic memory problems through its
The program in Figure 13 has an error in calling operator 1: #include <iostream.h> 2: #include <stdlib.h> 3: #include <string.h> 4: #define SIZE 128 5: 6: class store{ 7: public: 8: store(int sz=24){size = sz;} 9: ~store(){size=0; cout << "Deleting:" << ptr ;} 10: int copy(char *src){ 11: int len; 12: 13: len = strlen(src); 14: if(len > size)return(0); 15: strcpy(ptr,src); 16: return(len); 17: } 18: protected: 19: char ptr[SIZE]; 20: int size; 21: }; 22: 23: main() 24: { 25: class store *first; 26: int limit=5,i; 27: char local[128]; 28: 29: first = new store[limit]; 30: for(i=0;i<limit;i++){ 31: sprintf(local,"Element %d\n",i); 32: first[i].copy(local); 33: } 34: delete first; 35: } When this program is compiled and run with Insure++, a "delete mismatch" error is reported, as shown in Figure 14. [bracket.C:33] **DELETE_MISMATCH** >> delete first; Inconsistent usage of delete operator: first array deleted without [] Stack trace where the error occurred: main() bracket.C, 33 4.1.5 StringsThough the standard C library string handling functions are useful, unfortunately they are also a rich source of potential errors. They do very little checking on the bounds of the objects being manipulated. Insure++ detects most string-related problems such as overwriting the end of a buffer and using strings without null terminators. 4.2 Programming and Third-Party Library Interface ErrorsLike memory reference errors, programming errors act as land mines in the program. When executed, programs containing them encounter problems ranging from incorrect values to system crashes. Third-party errors are particularly tricky to handle. When a program crashes in the third-party code, it might be because either the library was passed incorrect parameters by the user or there is an actual bug in the third-party code. Programming errors, and library interface errors in particular, can also cause difficulties porting code across platforms due to architectural idiosyncrasies. Insure++ is able to discover both of these types of problems and provide diagnostics about which of the problems occurred. Providing this type of information is critical because source code for the third-party library is generally not available, and it is not enough just to say that the bug occurred in the library. If the bug in the third-party library was caused by passing incorrect parameters, you can easily remedy it. But if the bug is caused by a fault in the library, then all that can be done is report it to the vendor. Insure++ can discover bugs in the third-party library even if the source code to the library is not available. The bugs are discovered by the code that Insure++ links to the application. When the third-party library executes, the Insure++ library checks the code in the third-party library for memory overwrites, dynamic memory problems, and more. 4.2.1 Data Representation and Variable Declaration ProblemsMany programs make either explicit or implicit assumptions about the various data types on which they operate. On many workstations, pointers and integers have the same number of bytes. While some of these problems can be detected during compilation, some codes go to great lengths to hide these problems with typecasts such as: char *p; int ip; ip = (int)p; On many systems, this type of operation is valid and causes no problems. However, problems can arise when this code is ported to other architectures. For example, the code shown above will fail when executed on a PC (16-bit integer, 32-bit pointer) or a 64-bit architecture such as DEC TruUnix64 (32-bit integer, 64-bit pointer). In cases where the operation loses information, Insure++ will report an error. On machines for which the data types have the same number of bits, no error is reported. Insure++ also detects inconsistent declarations of variables between source files. For example, an object might be declared as an array in one file, but as a pointer in another. Insure++ reports size differences so that an array declared as one size in one file and another in a second will be detected. 4.2.2 I/O Statements
The
In addition to checking foo(line) char line[80]; { gets(line); } works as long as the input supplied by the user is shorter than 80 characters, but fails on longer input. Insure++ checks for this case and reports an error if necessary. 4.2.3 Mismatched ArgumentsCalling functions with incorrect arguments is a common and often overlooked problem in many programs. Insure++ automatically detects the argument mismatches described below.
4.2.4 Invalid Parameters in System CallsInterfacing to library software is often tricky because passing an incorrect argument to a routine might cause it to fail inconsistently. Debugging such problems is much harder than correcting your own code since you typically have much less information about how the library routine should work. Insure++ has built-in knowledge of a large number of system calls and checks the arguments to ensure correct data type and, if appropriate, range. For example, the code myrewind(fp) FILE *fp; { fseek(fp, (long)0, 3); }
will cause an error, since the last argument passed to the Insure++ includes built-in interface tests for hundreds of libraries. You can construct additional interface checks easily with Insure++'s interface definition features. 4.2.5 Unexpected Errors in System CallsChecking return codes from system calls and dealing correctly with all the possible error cases that can arise is very difficult. Exhaustive testing of all the possible combinations is almost impossible. As a result, programs can fail unexpectedly because some system call fails in a way that had not been anticipated. The consequences can range from a "core dump" to an infrequent, unrepeatable error.
Insure++ has a special error class,
Insure++ understands standard UNIX and Windows system calls, the X Window System, Motif, and many other popular libraries. 4.3 Errors Specific to C++Insure++ uncovers a number of errors specific to the C++ language, including memory allocation conflicts and inconsistent usage of the delete operator. 4.3.1 Inconsistent Usage of Delete Operator
The current version of ANSI C++ distinguishes between memory allocated with
Calling
The code in Figure 15 shows a block of memory allocated with 1: /* 2: * File: delmis1.cpp 3: */ 4: 5: int main() { 6: int *a = new int [5]; 7: delete a; 8: return 0; 9: } When this program is compiled and run with Insure++, a "delete mismatch" error is reported, as show in Figure 16. [delmis1.cpp:7] **DELETE_MISMATCH** >> delete a; Inconsistent usage of delete operator: a array deleted without [] a, allocated at: main() delmis1.cpp, 6 Stack trace where the error occurred: main() delmis1.cpp, 7 4.3.2 Memory Allocation
This error is generated when a memory block is allocated with
Some compilers allow this, but it is not a good programming practice and might cause a problem with portability.
The code in Figure 17 shows a typical example of this error, allocating a block of memory with 1: /* 2: * File: alloc2.cpp 3: */ 4: #include <stdlib.h> 5: 6: int main() { 7: char *a; 8: 9: a = (char *) malloc(1); 10: delete a; 11: return 0; 12: } When this program is compiled and run with Insure++, a "memory allocation conflict" error is reported, as show in Figure 18. [alloc2.cpp:10] **ALLOC_CONFLICT** >> delete a; Memory allocation conflict: a delete operator used to deallocate memory not allocated by new block allocated at: malloc()(interface) main()alloc2.cpp, 9 Stack trace where the error occurred: main()alloc2.cpp, 10 5. ConclusionEven programs that compile, produce correct results, and have a large commercial distribution can contain elusive errors such as memory references and memory leaks. Insure++ can detect these errors during development and prevent them from holding up a project, or appearing at a user site. 6. AvailabilityInsure++ is available now at . To learn more about how Insure++ and other ParaSoft development tools can help your department prevent and detect errors, talk to a Software Quality Specialist today at 1-888-305-0041 (U.S.A. only), or visit . 6.1 PlatformsInsure++ is available for the following platforms (64-bit support is available on selected platforms).
6.2 Compiler CompatibilityInsure++ works with all popular compilers. Insure++ can also check modules written in languages other than C++, such as Fortran, Ada, and Pascal. 7. Contacting ParaSoftUSA
2031 S. Myrtle Ave. Europe
France: Tel: (33 1) 64 89 26 00 |

| (888) 305-0041 info@parasoft.com Copyright © 1996-2001 ParaSoft |