Sharing and Mounting Files with Kerberos Authentication
Before you can share a file system from the server and mount file systems on clients with Kerberos authentication, Kerberos Version 4 authentication must be enabled on the network.
To share a file system with Kerberos authentication, you specify the -o sec=krb4 option to the share command:
- 1. On the server, become superuser.
- 2. Type share -F nfs -o sec=krb4 /<filesystem> and press Return.
To mount a file system with Kerberos authentication, you specify the -o sec=krb4 option to the mount command:
- 1. On the client, become superuser.
- 2. Check to make sure the mount point exists. If not, type mkdir <directory-name> and press Return to create the mount point.
- 3. Type mount -F nfs -o sec=krb4 <server>:<resource> <mountpoint> and press Return.
Logging In to Kerberos Service
You log in to the Kerberos service by using the kinit -l<username> command.
To log in to the Kerberos service:
- 1. Type kinit -l <username> and press Return.
- 2. Type the number of minutes you want the Kerberos ticket to be valid.
- 3. Type your password.
In the following example, user ray logs in to Kerberos service with a ticket lifetime of 60 minutes:
seachild% kinit -l ray
SunOS (seachild)
Kerberos Initialization for "ray"
Kerberos ticket lifetime (minutes): 60
Password:
seachild%
Listing Kerberos Tickets
You list tickets by using the klist command. The following example shows a ticket for user ray.
seachild% klist
Ticket file: /tmp/tkt8765
Principal: ray@Castle.Abc.COM
Issued Expires Principal
Oct 10 15:15:56 Oct10:16:15:56 krbtgt.Castle.Abc.COM@Castle.Abc.com
Accessing a Directory with Kerberos Authentication
You access a Kerberos mounted directory just as you would any other mounted directory: by typing cd /<mountpoint>. You can list the files in the directory by using the ls command or list the Kerberos tickets by using the klist command.
Destroying a Kerberos Ticket
You destroy Kerberos tickets by using the kdestroy command. You should destroy Kerberos tickets when the session is over so that an unauthorized user cannot gain access to them. If you want to reinitiate Kerberos authentication after tickets are destroyed, use the kinit command.
The following example shows how to destroy Kerberos tickets. After the tickets are destroyed, if the user tries to change to or list a Kerberos-protected directory, the ticket server denies access.
seachild% kdestroy
Tickets destroyed
seachild% ls /mntkrb
Can't get Kerberos key: No ticket file (tf_util)
NSF getattr failed for server castle: RPC: Authentication error
cannot access directory /mntkrb.
seachild%
The Pluggable Authentication Module (PAM) Framework
 PAM enables you to "plug in" new authentication technologies without changing system entry services such as login, ftp, telnet, and so on. You can also use PAM to integrate UNIX login with other security mechanisms such as DES or Kerberos. You can also plug in mechanisms for account, session, and password management by using this framework. The PAM framework enables you to choose any combination of system entry services (for example, ftp, login, telnet, or rsh) for user authentication.
PAM enables you to "plug in" new authentication technologies without changing system entry services such as login, ftp, telnet, and so on. You can also use PAM to integrate UNIX login with other security mechanisms such as DES or Kerberos. You can also plug in mechanisms for account, session, and password management by using this framework. The PAM framework enables you to choose any combination of system entry services (for example, ftp, login, telnet, or rsh) for user authentication.
PAM Module Types
PAM employs run-time pluggable modules to provide authentication for system entry services. These modules are broken down into four different types based on their function:
- • The authentication modules provide authentication for users and enables credentials to be set, refreshed, or destroyed. They provide a valuable administration tool for user identification.
- • The account modules check for password aging, account expiration, and access hour restrictions. After the user is identified through the authentication modules, the account modules determine if the user should be given access.
- • The session modules manage the opening and closing of an authentication session. They can log activity or provide for clean-up after the session is over.
- • The password modules enable changes to the actual password.
Stacking Feature
A stacking feature is provided to let you authenticate users through multiple services. Depending on the configuration, users can be prompted for passwords for each authentication method. The order in which the authentication services are used is determined through the PAM configuration file, /etc.pam.conf.
Password-Mapping Feature
The stacking method can require that a user remember several passwords. With the password-mapping feature, the primary password is used to decrypt the other passwords so that the user does not need to remember or enter multiple passwords. The other option is to synchronize the passwords across each authentication mechanism. Note that synchronizing passwords can increase the security risk, because the security of each mechanism is limited by the least secure password method used in the stack.
How PAM Works
The PAM software consists of a library, several modules, and a configuration file. New versions of several system entry commands or daemons that take advantage of the PAM interfaces are also included.
Figure 19-1 shows the relationship between the applications, the PAM library, the pam.conf file, and the PAM modules.
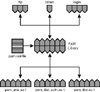
Figure 19-1 How PAM works.
The ftp, telnet, and login programs use the PAM library to access the appropriate module. The pam.conf file defines which modules to use, and in what order they are to be used with each command. Responses from the modules are passed back through the library to the application.
 PAM enables you to "plug in" new authentication technologies without changing system entry services such as login, ftp, telnet, and so on. You can also use PAM to integrate UNIX login with other security mechanisms such as DES or Kerberos. You can also plug in mechanisms for account, session, and password management by using this framework. The PAM framework enables you to choose any combination of system entry services (for example, ftp, login, telnet, or rsh) for user authentication.
PAM enables you to "plug in" new authentication technologies without changing system entry services such as login, ftp, telnet, and so on. You can also use PAM to integrate UNIX login with other security mechanisms such as DES or Kerberos. You can also plug in mechanisms for account, session, and password management by using this framework. The PAM framework enables you to choose any combination of system entry services (for example, ftp, login, telnet, or rsh) for user authentication.